Basic Cloud Fundamentals
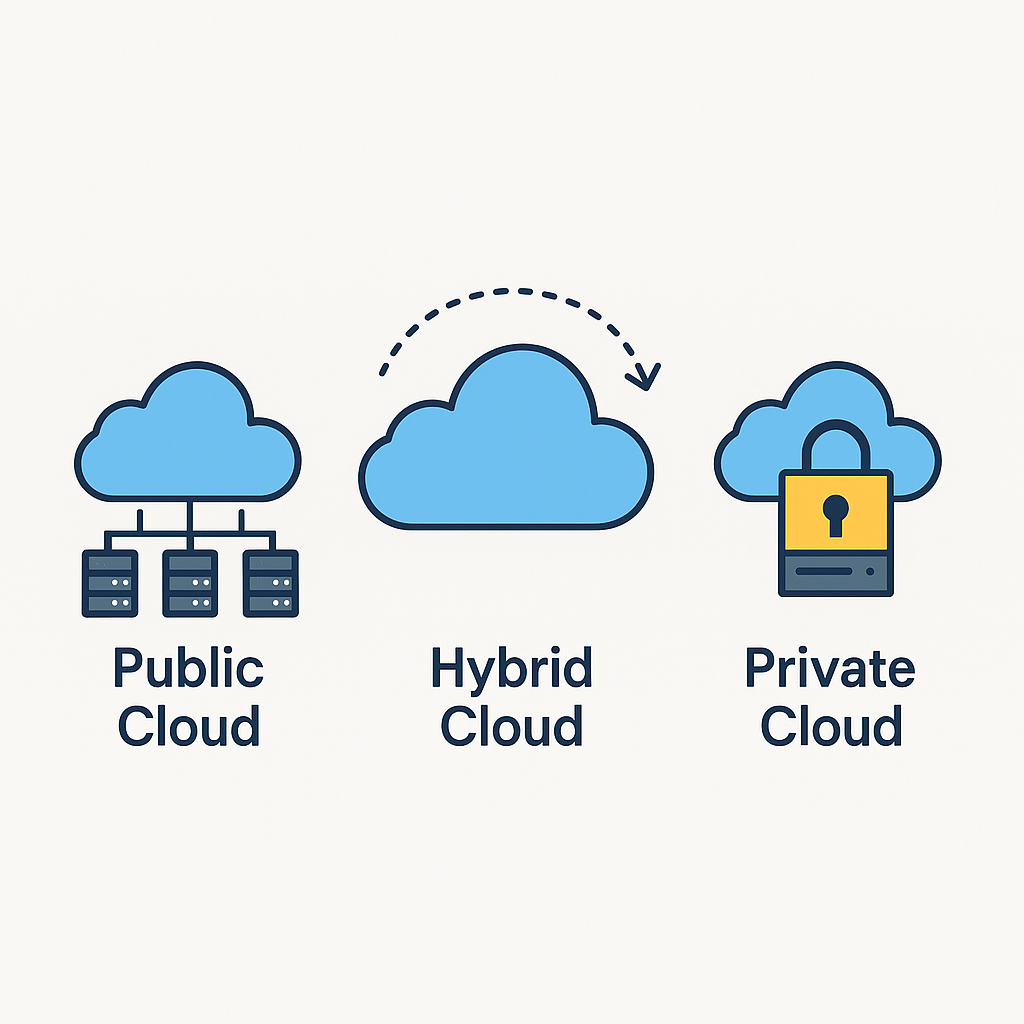
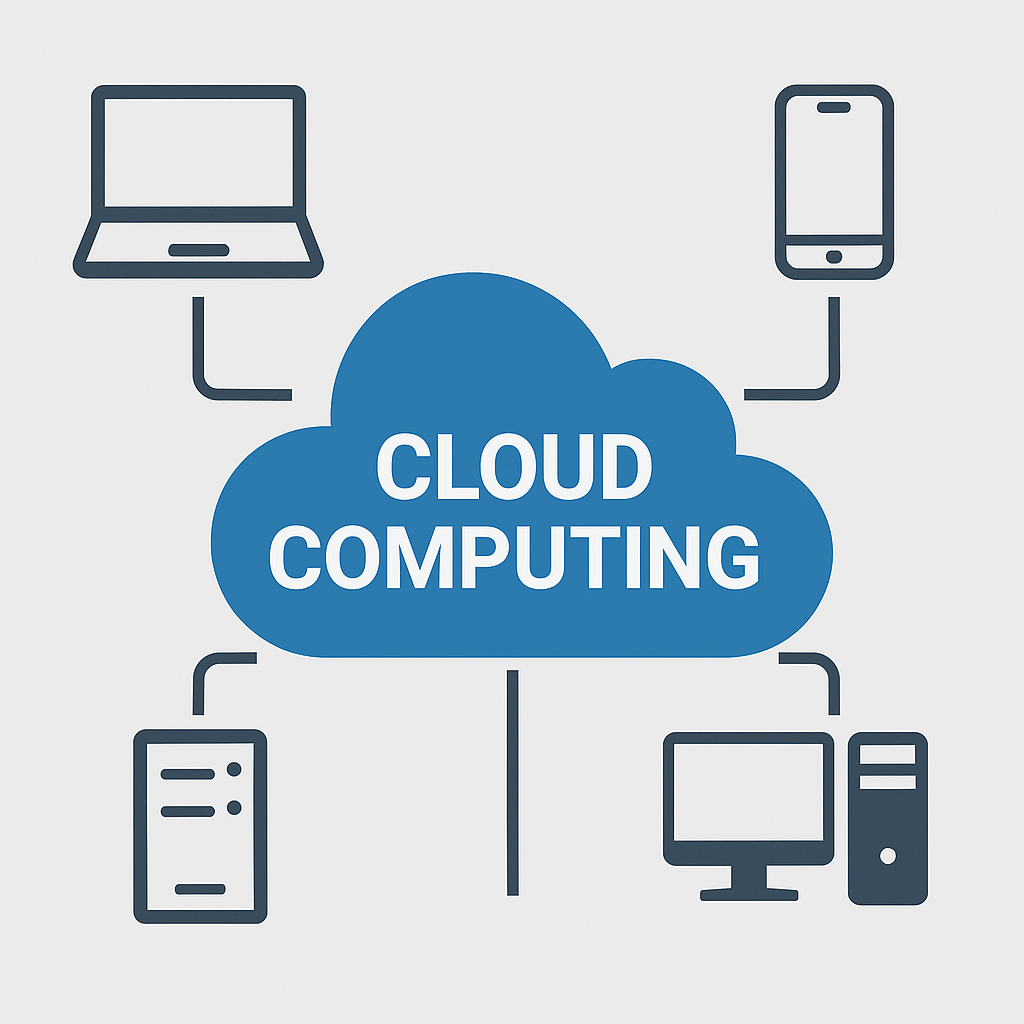
Cloud computing has revolutionized how organizations provision, deploy, and manage IT resources. Instead of maintaining physical servers, storage, and networking hardware on-premises, users can access a shared pool of configurable computing resources over the internet. This “as-a-service” model provides on-demand scalability, pay-per-use billing, and rapid elasticity to support dynamic workloads and accelerate innovation.
 OpenPath
OpenPath